-

International Cryptographic Module Conference 2019 in Vancouver, Canada
After a day of pre-conference workshops, the 7th International Cryptographic Module Conference (ICMC) was kicked off this morning with a welcome address from atsec’s VP and Lab Director Yi Mao. (from left to right: Renaudt Nunez, Stephan Mueller, Fiona Pattinson, Swapneela Unkule, Yi Mao) Yi Mao’s Opening Speech…
-

International Cryptographic Module Conference 2018 in Ottawa, Canada
After a day of pre-conference workshops, the International Cryptographic Module Conference (ICMC) 2018 was kicked off this morning with a welcome address from atsec’s VP and Lab Director Yi Mao. The welcome was followed by keynote speeches from Jason Hart, CTO of Data Protection for Gemalto UK and…
-

Yi Mao’s Opening Speech at the Fifth ICMC
“Dear Community, It is the second time that I have had the honor and pleasure to open the International Cryptographic Module Conference. This year is very special since it is the fifth anniversary of the conference. I’d like to welcome you all with an image from the end…
-
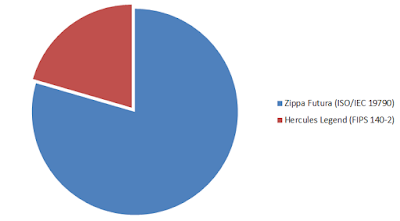
ICMC Presidential Debate
The votes have been counted and Zippa Futura and ISO/IEC 19790 win by a large margin:
-

The Third International Cryptographic Module Conference Has Begun
The 2015 International Cryptographic Module Conference (ICMC) started yesterday with a day of pre-conference workshops on FIPS 140 Projects, Breaking into Embedded Devices, and Addressing Unique Security Challenges through Standardization. The main conference was opened today by Yi Mao, Ph.D., CST Lab Manager of atsec, followed by keynote…
-

The Second International Cryptographic Module Conference
The 2014 ICMC started with a day of workshops on FIPS 140-2 and ISO/IEC 19790, followed today by keynote speakers Helmut Kurth (atsec information security) and Mary Ann Davidson (Oracle). Almost 200 attendees from around the world came to this year’s conference to discuss topics ranging from high-level…
-

Collaboration and Openness to the Rescue of Entropy
This past September was my conference month. I first went to the 14th International Common Criteria Conference (ICCC) in Orlando, Florida and then a week later I was at the 1st International Cryptographic Module Conference (ICMC) in Gaithersburg, Maryland. The theme of the ICCC this year was a…
-

A Summary of the First ICMC
The first ICMC is over.It was a wonderful event and thanks are due to all of the 171 participants for making it so. Participant Quote: “This conference is Win Win Win!”These attendees represented developers, governments, laboratories, consultants, and academics from the cryptographic module community. It turned out to…
-
Call for Papers: The First International Cryptographic Module Conference (ICMC 2013)
This first ICMC aims to bring together experts from around the world to confer on the topic of cryptographic modules, with emphasis on their secure design, implementation, assurance, and use, referencing both new and established standards such as FIPS 140-2 and ISO/IEC 19790. We are focused on attracting…
