-
atsec’s Yi Mao Interviewed on the TopCyberPro Podcast
Dr. Yi Mao speaks with TopCyberPro host Jim West about the Common Criteria, FIPS, and more.
-

Exciting Milestone: First atsec Cybersecurity Certificates Issued for Common Criteria
atsec’s Certification Body has issued its first Common Criteria certificates!
-

First Post Quantum Cryptographic Algorithm Certificates Issued
With the arrival of the first post-quantum cryptographic algorithms, atsec is ready to provide testing services for them.
-
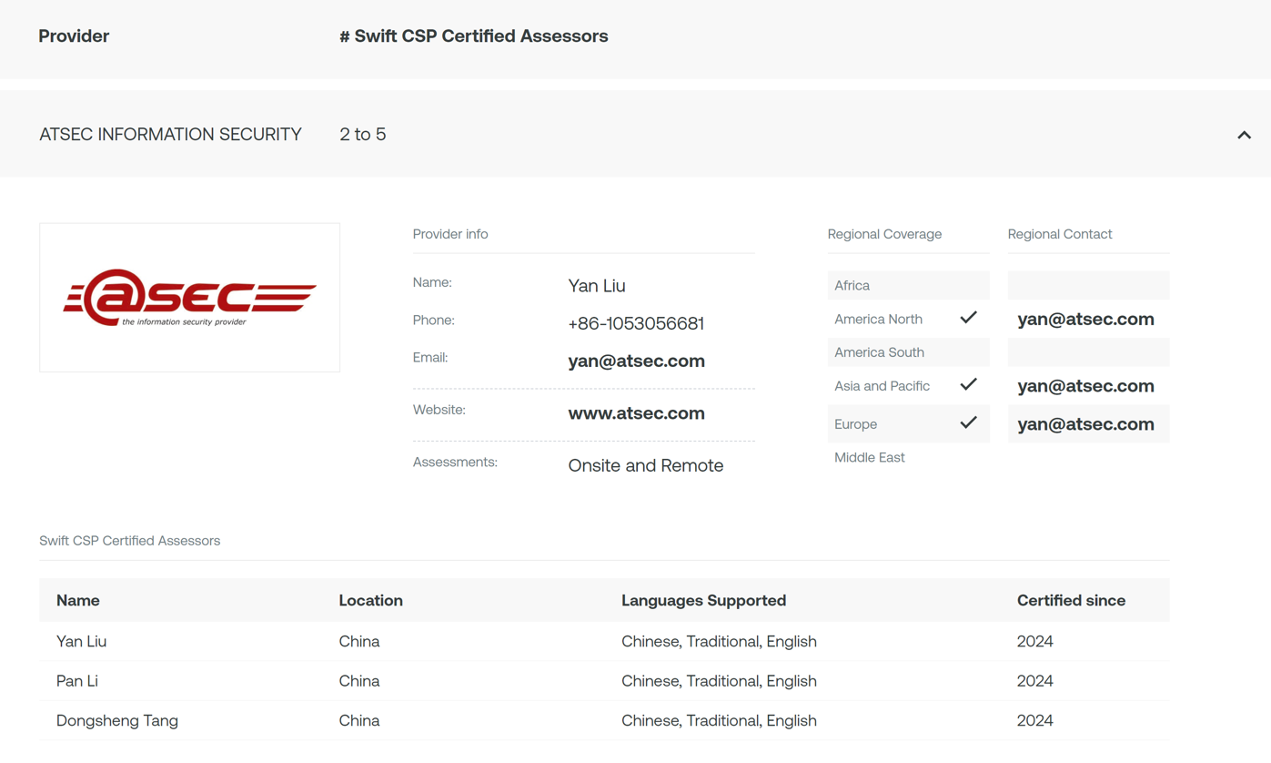
atsec Adds Swift CSP Assessment Qualification
As a Swift CSP Assessment Provider, atsec can assess compliance with CSP mandatory and advisory controls.
-

Guiding the Way through the World of Cyber Security
Looking back on 25 years of cybersecurity excellence, and looking forward to more.
-

EUCC and Cybersecurity Certification in Europe
The European Union Agency for Cybersecurity hosted a Cybersecurity Certification Conference – here are the key takeaways.
-

atsec AB first IEEE 2621 Accredited Medical Device Testing Facility
atsec Sweden has been approved as an IEEE Authorized Testing Facility – we can now test medical devices according to the IEEE 2621 standard!
-

Cybersecurity Requirements for Medical Devices
The IEEE established a Medical Cybersecurity Certification Program, and atsec is the first IEEE recognized testing lab!
-

Artificial Intelligence in Evaluation, Validation, Testing and Certification
AI is becoming increasingly prevalent and powerful – how is atsec planning to use it?
