
by Andreas Fabis
When we talk to our customers about FIPS 140-2 testing some questions regarding certificate maintenance frequently come up:
- “What happens to my certificate if I make changes to my module?”
- “Do I have to re-certify every single time I make a small change?”
- “What if we want to patch a vulnerability?”
There are many factors that can lead to module or platform changes: technical, business and marketing, to name a few. Navigating the rules and options of FIPS 140-2 re-certification can be challenging, and currently there are additional factors and deadlines to consider:
- The switch from FIPS 140-2 to FIPS 140-3 (mandatory after September 22nd 2021)
- The switch from the Cryptographic Algorithm Validation System (CAVS) to the Automated Cryptographic Validation Testing (ACVT) (mandatory after June 30th 2020)
- The switch from FIPS I40-2 IG 7.15 to SP 800-90B compliance (mandatory after November 8th 2020)
From a FIPS 140-2 point of view, the exact details of the re-certification process and the requirements for the different re-certification scenarios are explained in G.8 of the FIPS 140-2 Implementation Guidance (IG). This article is intended to help customers understand the practical implications of the different scenarios.
Non-security-relevant changes to the module or changes to the platform
Changes to hardware, software or firmware components that do not affect any security relevant items within the module are covered by scenario 1 (also known as a 1-SUB). Changing the module platform (for a software module) or adding a new platform to an existing module are also common scenarios for 1-SUBs. The laboratory will review the vendor’s documentation to make sure that no security relevant items are affected by either the change of module or the change of platform. In case of changing or adding a new platform, the module needs to be tested on the new platform. The lab then submits a package to the Cryptographic Module Validation Program (CMVP) that contains a letter explaining the nature of the change, the laboratory’s assessment and—depending on the changes—an updated Security Policy and/or draft certificate. Upon the approval of 1-SUB, the existing FIPS certificate will be updated to reflect the new version of the module or the new platform(s). The certificate expiration date remains the same.
Another option is to add the new platform as a vendor affirmed platform. These platforms will not be listed on the certificate itself, but in the Security Policy that is attached to the certificate listing. Vendor affirmation is not backed up by the CMVP and hence does not carry as much weight as laboratory testing and validation. It is up to the customer whether they accept a vendor’s claim that the module works as expected on the affirmed platforms.
Security relevant changes to the module
If there are security relevant changes to the module itself the submission scenario depends on the amount of changes. If the changes are relatively minor (less than 30%), scenario 3 (3-SUB) is applicable. This means that the laboratory will assess the amount and nature of the changes, then perform the applicable testing to make sure the affected security functions still work as expected. The laboratory will submit a test report to the CMVP and upon positive review a new certificate will be issued which is valid for 5 years.
Scenario 3A (3A-SUB) is specifically meant to address vulnerability patches if the vulnerability is on the official CVE list. In this case the CMVP waives the NIST fee as an incentive to vendors to patch vulnerabilities. The laboratory will perform the applicable regression testing and submit an updated test report. The CMVP will process the 3A-SUB at the speed of 1-SUB. In this case the existing certificate will be updated and the certificate expiration date remains the same.
If the amount of security-relevant change is above 30%, the module will be submitted under scenario 5 (5-SUB) which is equivalent to a new validation.
A quick summary of the most common re-certification scenarios: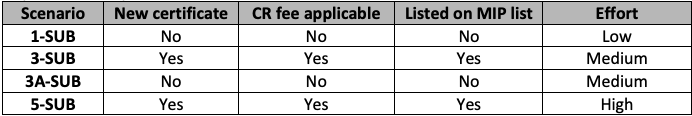
What about FIPS 140-3?
Modules tested under FIPS 140-2, and their reports submitted before September 22nd 2021, once validated, will stay valid for 5 years. Once FIPS 140-3 has become mandatory, any re-validation of a module validated under FIPS 140-2 will automatically be a 5-SUB under FIPS 140-3.
Strategies
The best validation strategy depends on the business needs, development cycles and other variables and may include:
- Re-validation of major releases only
- Re-validation every 6 or 12 months (accumulate changes)
- Re-validation based on customer demand
- Re-validation to patch critical vulnerabilities
In the end the best course will be different for every organization. As a laboratory we can help you find the best solution for your particular needs.



