Certification
Common Criteria
Product Certification
Consult our experts. We are happy to support you.
The Common Criteria (CC), also known as ISO 15408, is an internationally recognized standard used to specify and assess the security of IT products. The CC standard does this by providing a set of general but rigorous functional and assurance criteria by which a product’s security aspects can be evaluated using the standard companion evaluation methodology ISO 18045. This allows for an objective verification of the trustworthiness of an IT product’s security.
What atsec offers:
atsec Sweden operates a private Certification Body, atsec CB, accredited by SWEDAC, Sweden’s national accreditation body, against requirements specified in the ISO/IEC 17065 standard. The scope of accreditation includes certification according to:
- the European Cybersecurity Certification Scheme (EUCC) at the assurance level Substantial and High
- our own Common Criteria Certification scheme based on Common Criteria ISO standards 15408 and 18045
atsec CB provides these services in conjunction with accredited ISO 17025 laboratories. Details for atsec’s accreditation and approvals can be found on our certificates page.
If you’re interested in an EUCC certification, get in touch and we will guide you through the certification process and provide you the certification application forms.
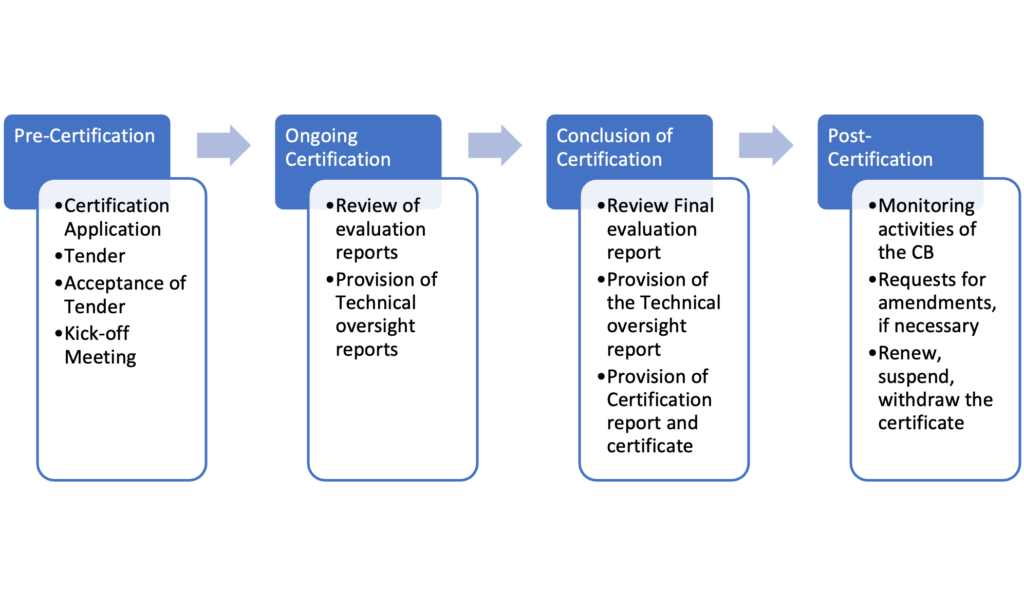
Why our services are important to you:
Certification done by a commercial Certification Body is often a faster and more flexible way of obtaining a certificate that meets the same high standards as certificates issued by government Certification Bodies.
Completed certifications:
Ongoing certifications:
| Certification ID | Vendor / Product (Product Type) | Scheme | Assurance Level | Status |
|---|---|---|---|---|
| ATSEC-EUCC-2026-004 | Nokia Solutions and Networks Oy Nokia Lightspan MF-8 and MF-14 (Network Product) | EUCC | Substantial/EAL3+ | Active |
| ATSEC-EUCC-2026-003 | Nokia Solutions and Networks Oy Nokia Lightspan MF-2 (Network Product) | EUCC | Substantial/EAL3+ | Active |
| ATSEC-EUCC-2026-002 | Nokia Solutions and Networks Oy Nokia ISAM 7360 FX (Network Product) | EUCC | Substantial/EAL3+ | Active |
| ATSEC-EUCC-2026-001 | Sectra Communications AB Sectra Gateway (Network Product) | EUCC | High/EAL4+ | Active |
| ATSEC-EUCC-2025-005 | Arbit Cyber Defence Systems ApS Arbit Trust Gateway Void Guard (ATGVG) (Software Application) | EUCC | High/EAL4+ | Active |
| ATSEC-EUCC-2025-004 | Sectra Communications AB Sectra Remote Connect for Windows (Software Application) | EUCC | High/EAL4+ | Active |
| ATSEC-EUCC-2025-003 | Huawei Technologies Co., Ltd Huawei OSN9800 (Network Product) | EUCC | Substantial/EAL3+ | Active |
| ATSEC-EUCC-2025-002 | Huawei Technologies Co., Ltd Huawei OSN1800&DC908 (Network Product) | EUCC | Substantial/EAL3+ | Active |
| ATSEC-EUCC-2025-001 | Blancco Oy Ltd Blancco File Eraser 8.6.3 (Software Application) | EUCC | Substantial/EAL2+ | Active |

Still have questions?
Can’t find what you’re looking for? Let’s talk!
Common Criteria Evaluation
The Common Criteria (CC), also known as ISO 15408, is an internationally recognized standard used to specify and assess the security of IT products.
Cryptographic Algorithm Testing
Testing that cryptographic algorithms are implemented correctly is a prerequisite for FIPS 140-3 cryptographic module testing and NIAP Common Criteria evaluations.
Entropy Source Assessment
Documented conformance, where applicable, to the SP 800-90B is required by the CMVP for all FIPS 140-3 module validation submissions.
The Information Security Provider
Read Our Latest Blog Articles
Learn the latest and greatest about information security. You’ll find insights and analyses of recent developments in technology and policy on our blog.
-

atsec’s Experience at the Post-Quantum Cryptography Workshop at the KTH Royal Institute of Technology
The PQC Workshop at the KTH Royal Institute of Technology was a trove of valuable insights.
-

Happy Valentine’s Day
We wish a Happy Valentine’s Day to all our colleagues, customers, suppliers and all their families and loved ones.

