-
You Raise Me Up – ICMC 2020
It has become an atsec tradition to produce an animation with an FIPS-relevant topic for the ICMC. This year it has the transition from FIPS 140-2 to FIPS 140-3 as the subject – with a personal touch. Yi Mao presented the animation during her opening speech at the…
-

Transitioning to NIST SP 800-56A Rev3: what you need to know
by Swapneela Unkule NIST SP 800-56A provides recommendations for Pair-Wise Key-Establishment Schemes Using Discrete Logarithm Cryptography. Diffie-Hellman (DH), Elliptic Curve DH (ECDH) and Menezes-Qu-Vanstone (MQV) key-agreement schemes are specified in this standard. These Key-Agreement Schemes (KAS) are widely used in network protocols such as TLS. The SP 800-56A…
-
Congratulations to Qualcomm
One of the rewards of working in the evaluation and testing business is to see our customers succeed and show the results of their efforts. We are always happy to work with organizations who are committed to IT security and want to improve their products and processes for…
-
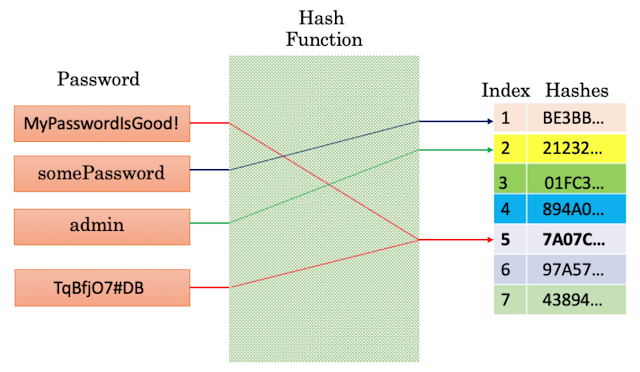
Rise & Fall of MD5
by Richard FantThe RiseMD5 (message digest version 5) was developed in 1991 and is still very popular today, with a wide range of commercial and government applications. MD5 is used to generate hash values of passwords stored on a system as opposed to storing the passwords in plain…
-
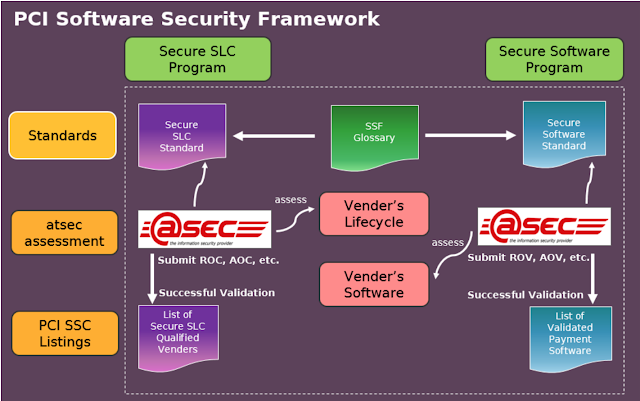
atsec China adds two PCI SSF Assessor Qualifications
atsec China has been qualified by the PCI SSC (Payment Card Industry Security Standards Council) as a Secure Software Lifecycle (SLC) Assessor and Secure Software Assessor company under the PCI Software Security Framework (SSF) program to evaluate a vendor’s software lifecycle and/or validate a vendor’s payment software. The…
-

Meltdown Attack: 2 Years Later
by Richard Fant Meltdown Attack: 2 years laterIn February 2017, independent security researchers discovered a catastrophic security flaw in the cache design for processors developed by Intel Corporation. After embargoing the information for almost a year while working on a fix, Intel publicly announced in January 2018 the…
-
atsec presented at InnoTech Austin 2019
atsec US Corporate Vice President and Lab Director, Yi Mao, presented “Crypto Testing Leading to Better Security” at InnoTech Austin 2019. Through many examples, Dr. Mao showed the audience that cryptography is the hard core providing data confidentiality, integrity and authenticity. Cryptographic algorithms are used to encrypt sensitive…
-

How can OpenSSL survive FIPS 140-2 validation in 2020?
by Stephan MuellerThe OpenSSL project outlined the development strategy pertaining to the Federal Information Processing Standard (FIPS) 140-2 code in the November 7th, 2019 OpenSSL blog titled “Update on 3.0 Development, FIPS and 1.0.2 EOL.”[1] As a summary, the following relevant aspects for FIPS 140-2 are communicated. · The…
-

atsec at the International Common Criteria Conference (ICCC) 2019
atsec participated in ICCC 2019 held in Singapore from October 1st to 3rd in conjunction with Singapore International Cyber Week (SICW). It was the perfect venue to celebrate the 20th anniversary of the Common Criteria standard with an increase of the Common Criteria Recognition Arrangement (CCRA) membership from…
