-

Now is the Time: Embracing the ACMVP at a Critical Crossroads
The ACMVP will arrive much sooner than expected.
-

BSI’s Study Analyzing RBG Usage in Browsers
atsec conducted a study for the BSI on the use of RBGs in internet browsers.
-

Digging into some FIPS ‘n’ Chips
atsec’s FIPS ‘n’ Chips crypto module bootcamp wrapped up this week, and it was a blast!
-
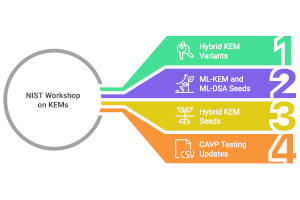
A Glimpse of the Future: NIST’s KEM Workshop
NIST held a workshop on the future of Key Encapsulation Mechanisms (KEMs), featuring several interesting proposals.
-

FIPS ‘n’ Chips Crypto Module Bootcamp
atsec and UT Austin are excited to host the second Crypto Module Bootcamp, free for all participants!
-

atsec Becomes the First Accredited EUCC Conformity Assessment Body
atsec is the first accredited EUCC Conformity Assessment Body!
-

atsec Adds GSMA MDSCert Evaluations to its Service Offerings
atsec now offers MDSCert evaluations for mobile device vendors!
-

atsec at the CCUF and ICCC24 in Qatar
atsec is attending the CCUF and ICCC24, where we’re excited to meet with colleagues from across the globe.
-

Strengthening IoT Security: The Role of SESIP Certification
SESIP is an important standard for IoT security, and atsec is now an approved laboratory for SESIP assessments.
